How To Stay Safe & Not Get Hacked
This
might be a good method to get rid of your system from being hacked or
your files from being stolen from your friends. May be your friend might
be trying to accessing your Windows account to get access to your
secret documents and information. You may not want to change password
regularly if you have the habit of forgetting. Well, in this tutorial I
am going to teach you how to log such failed attempts to your account.
By default Windows does not keep record of success and failure attempts. However you can check if it’s active or not by following steps:
Right click on My Computer Icon > Manage.
For Windows Vista or Later,
Go to System Tools> Even Viewer > Windows Logs > Security
For Windows XP,
Go to System tools > Event viewer > Security
You can see here about the Successful and Failed Login Attempts.
I’ve the above screen in my Windows 7. But windows may not be logging your login attempts. Therefore you’ll need to activate it from Group Policy editor.
To enable success and failed attempts do the following:
Load up RUN command, type gpedit.msc . It will load Group Policy Editor Window.
At the left policy explorer, go to Local Computer Policy > Computer Configuration > windows Settings> Security Settings> Local policies > Audit Logon Events .
At the right side of window, select ”Audit Policy Change “ and check on both ”Success” and ”Failure” Option.
Now press OK. You may now close the Group Policy Editor window.
Now Windows will be logging all your successful or failed login attempts.
To test if it works or not, create a test account, create password for it. Restart your PC. Try entering wrong password to your account few times. And again enter correct password. Window will load of.
Again right click on My Computer> Manage. Go to, System tools > Event viewer > Security
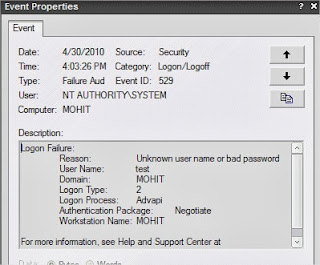
You’ll see the screen similar to this.
Double click on one of the failed attempts and it will show up the details.
Hope this was helpful tutorial to make your account more secure.
By default Windows does not keep record of success and failure attempts. However you can check if it’s active or not by following steps:
Right click on My Computer Icon > Manage.
For Windows Vista or Later,
Go to System Tools> Even Viewer > Windows Logs > Security
For Windows XP,
Go to System tools > Event viewer > Security
You can see here about the Successful and Failed Login Attempts.
I’ve the above screen in my Windows 7. But windows may not be logging your login attempts. Therefore you’ll need to activate it from Group Policy editor.
To enable success and failed attempts do the following:
Load up RUN command, type gpedit.msc . It will load Group Policy Editor Window.
At the left policy explorer, go to Local Computer Policy > Computer Configuration > windows Settings> Security Settings> Local policies > Audit Logon Events .
At the right side of window, select ”Audit Policy Change “ and check on both ”Success” and ”Failure” Option.
Now press OK. You may now close the Group Policy Editor window.
Now Windows will be logging all your successful or failed login attempts.
To test if it works or not, create a test account, create password for it. Restart your PC. Try entering wrong password to your account few times. And again enter correct password. Window will load of.
Again right click on My Computer> Manage. Go to, System tools > Event viewer > Security
You’ll see the screen similar to this.
Double click on one of the failed attempts and it will show up the details.
Hope this was helpful tutorial to make your account more secure.
.png)